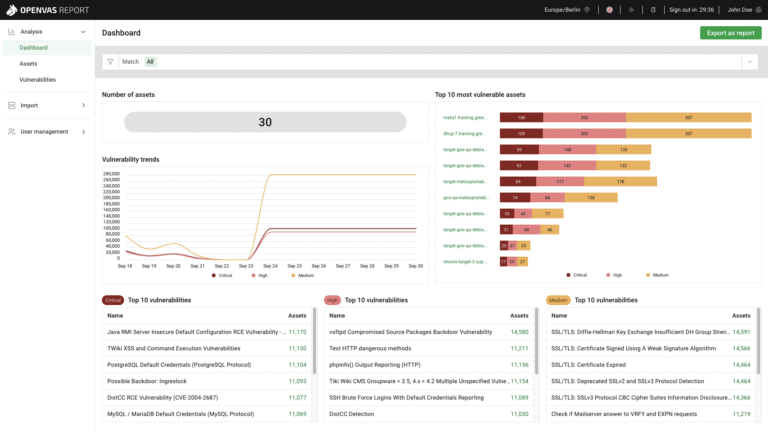
Network Scanning
Network scanning is one of the first and most important steps in protecting a computer network from cyber threats. It’s the process of examining a network to discover all connected devices, open ports, and running services—essentially creating a map of everything that’s online. For IT administrators, this is a vital tool that helps them understand what’s on their network, how it’s configured, and where vulnerabilities might exist. Hacking for Good uses network scans to identify outdated software, misconfigured systems, or unauthorized devices that could be exploited by hackers. In short, network scanning gives IT admins the visibility and control they need to keep their systems secure, efficient, and resilient against evolving cyber threats. Not familiar? No problem! Hacking for Good provides a custom appliance to conduct the scans- simply plug it in to your network, power it on, and walk away!

Network Traffic Inspection
Network traffic inspection is the process of monitoring and analyzing the data that flows in and out of a nonprofit’s computer network. This includes emails, web activity, file transfers, and other communications between devices and external servers. For nonprofits, inspecting network traffic is a vital cybersecurity measure that helps detect suspicious behavior, prevent data breaches, and protect sensitive information such as donor records, financial data, and internal communications. Cybercriminals often target nonprofits because they may have limited security resources but still handle valuable data. By examining traffic patterns, Hacking for Good can spot unusual activity like unauthorized access attempts or unsecured communication and recommend mitigations. Regular network traffic inspection strengthens a nonprofit’s overall security posture and builds trust with supporters by demonstrating a commitment to safeguarding their information.

Cyber Maturity Model Certification Self-Assessment
The Cybersecurity Maturity Model Certification (CMMC) framework is a set of cybersecurity standards developed by the U.S. Department of Defense (DoD) to ensure that contractors and subcontractors properly protect sensitive government informationOrganizations working with the federal government are required to meet specific CMMC levels based on the nature of their work, making it an essential part of doing business in the defense sector. While your organization may not hold federal contracts, the framework is a valuable benchmark for any organization looking to strengthen its cybersecurity posture. CMMC outlines three levels of maturity, and Hacking for Good can help run you through the Level 1 basic self-assessment that helps organizations understand their current security practices and identify areas for improvement. By adopting CMMC principles, businesses can reduce their risk of cyberattacks, improve resilience, and align with industry best practices.
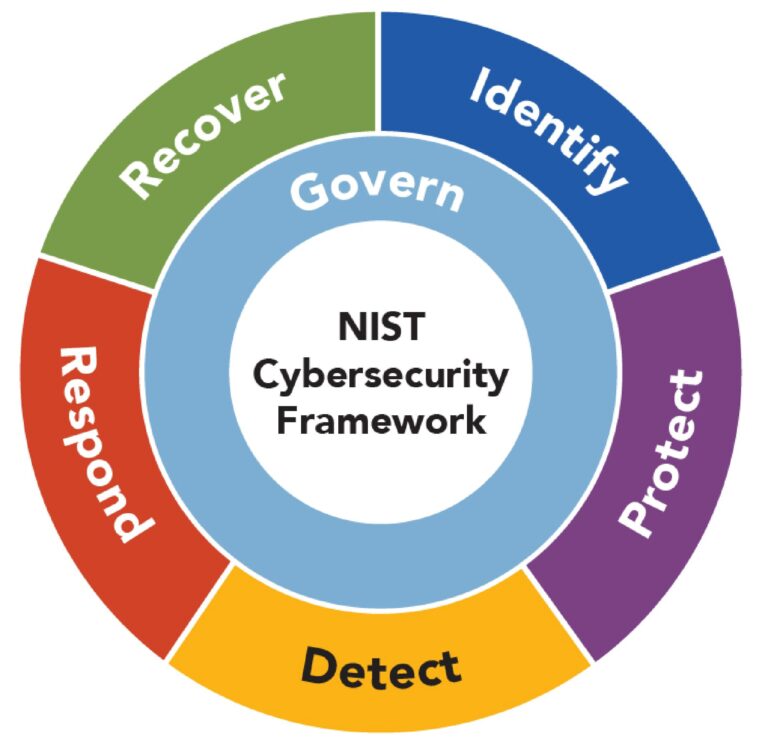
NIST Cybersecurity Framework
The NIST Cybersecurity Framework is a set of guidelines developed by the National Institute of Standards and Technology to help organizations manage and reduce cybersecurity risks. It provides a structured approach to identifying, protecting, detecting, responding to, and recovering from cyber threats, making it a widely accepted standard in cybersecurity planning. Hacking for Good can help your organization review and incorporate relevant practices from the framework to bolster your cybersecurity posture. Its importance lies in helping organizations build stronger defenses, improve incident response, and align their security practices with industry best practices. By following the framework, companies can better safeguard sensitive data, maintain customer trust, and meet regulatory requirements. Overall, the NIST Cybersecurity Framework serves as a valuable tool for building a resilient and proactive security posture in today’s increasingly digital world.

Policy Review
Everyone gets a login when they join an organization- what happens when they leave? Does everyone share the password to the company’s general inquiry email account? Can I connect my personal laptop to the company network? A cybersecurity policy review is a structured evaluation of an organization’s existing rules, procedures, and guidelines that govern how digital assets and sensitive information are protected. The process examines areas such as data privacy, access controls, password standards, incident response, and employee training to ensure they align with current best practices and regulatory requirements. By identifying gaps, outdated measures, or unclear responsibilities, the review helps strengthen resilience against cyber threats. Ultimately, it provides a roadmap for improving security posture, reducing risk, and fostering a culture of accountability and awareness across the organization, as well as ensuring leadership has clear, actionable guidance for making informed security decisions.

Online Footprint Review
An online footprint evaluation for a nonprofit is a cybersecurity-focused review of how much information the organization—and its staff, volunteers, and donors—are exposing publicly on the internet. This includes analyzing the nonprofit’s website, social media accounts, staff directories, event listings, and any other digital content that could reveal sensitive or exploitable details. While transparency is important for building trust, too much publicly available information can make the organization and its community easy targets for cybercriminals. For example, listing staff names and email addresses can enable phishing attacks, while sharing internal processes or donor data might open the door to social engineering. An evaluation helps nonprofits understand what attackers could learn just by looking online, and how that information might be used to craft convincing scams or gain unauthorized access. By identifying and reducing unnecessary exposure, nonprofits can better protect their users, safeguard sensitive data, and strengthen their overall cybersecurity posture.

Simulated Phishing Exercises
A simulated phishing exercise is a cybersecurity training method used to test and educate employees about phishing threats. Hacking for Good can send fake but realistic phishing emails to organizational staff to see how they respond-whether they click on suspicious links, enter sensitive information, or report the email as suspicious, all in a safe and controlled environment. The goal isn’t to trick or punish employees, but to raise awareness and improve their ability to recognize and avoid real phishing attacks. Phishing is one of THE MOST common ways cybercriminals gain access to networks, often leading to data breaches, financial loss, or system compromise. By running simulations, companies can identify weak spots in their defenses, provide targeted training, and build a culture of caution and vigilance. These exercises also help IT teams measure the effectiveness of their security awareness programs and reduce the overall risk of a successful attack.
