A simulated phishing exercise is a cybersecurity training method used to test and educate employees about phishing threats. Hacking for Good can send fake but realistic phishing emails to organizational staff to see how they respond-whether they click on suspicious links, enter sensitive information, or report the email as suspicious, all in a safe and controlled environment. The goal isn’t to trick or punish employees, but to raise awareness and improve their ability to recognize and avoid real phishing attacks. Phishing is one of THE MOST common ways cybercriminals gain access to networks, often leading to data breaches, financial loss, or system compromise. By running simulations, companies can identify weak spots in their defenses, provide targeted training, and build a culture of caution and vigilance. These exercises also help IT teams measure the effectiveness of their security awareness programs and reduce the overall risk of a successful attack.
Related Post
Online Footprint Review
An online footprint evaluation for a nonprofit is a cybersecurity-focused review of how much information the organization—and its staff, volunteers, and donors—are exposing publicly on the internet. This includes analyzing the nonprofit’s website, social media accounts, staff directories, event listings, and any other digital content that could reveal sensitive or exploitable details. While transparency is […]
The Cybersecurity Maturity Model Certification (CMMC) framework is a set of cybersecurity standards developed by the U.S. Department of Defense (DoD) to ensure that contractors and subcontractors properly protect sensitive government informationOrganizations working with the federal government are required to meet specific CMMC levels based on the nature of their work, making it an essential […]
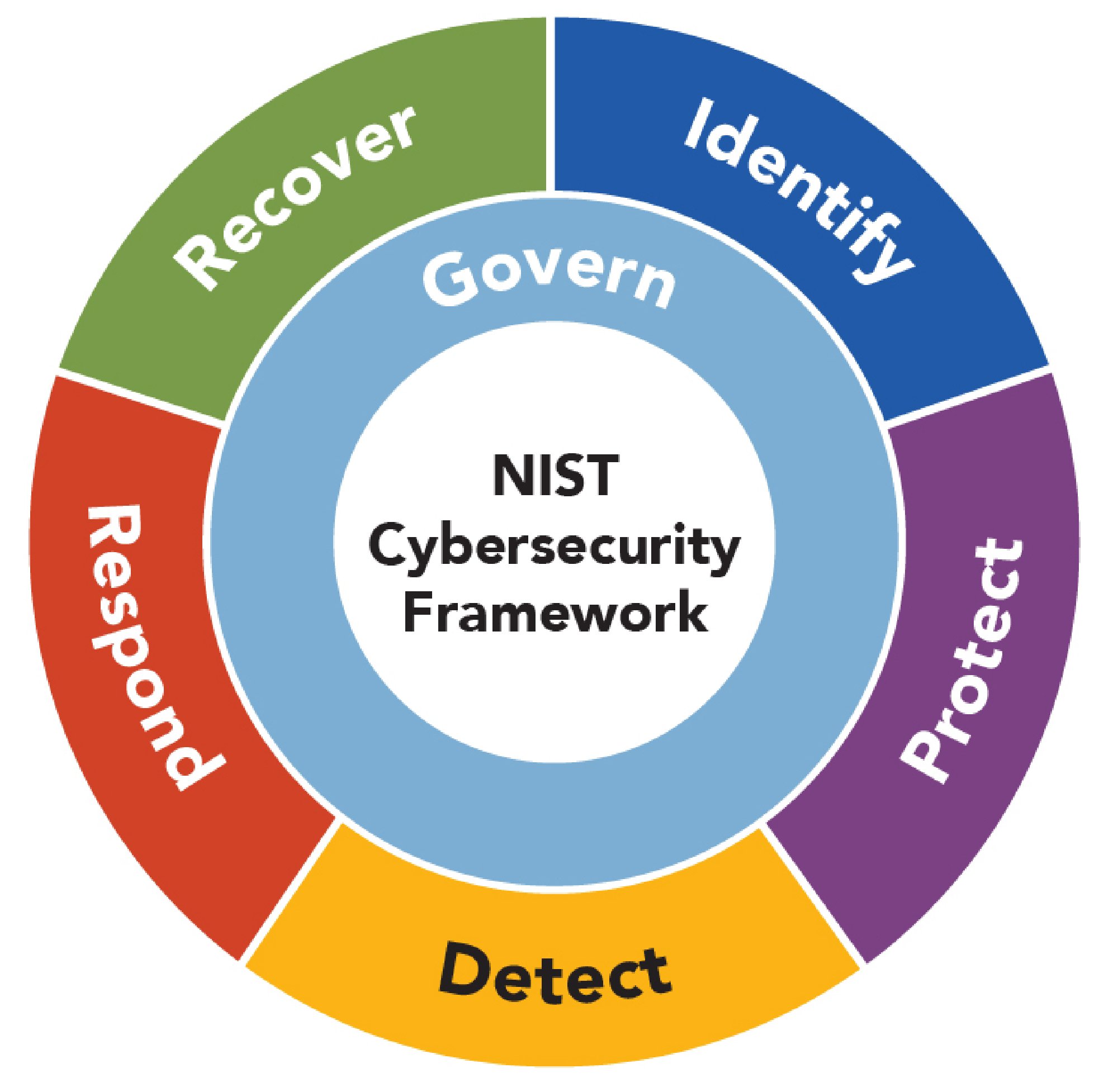
NIST Cybersecurity Framework
The NIST Cybersecurity Framework is a set of guidelines developed by the National Institute of Standards and Technology to help organizations manage and reduce cybersecurity risks. It provides a structured approach to identifying, protecting, detecting, responding to, and recovering from cyber threats, making it a widely accepted standard in cybersecurity planning. Hacking for Good can […]