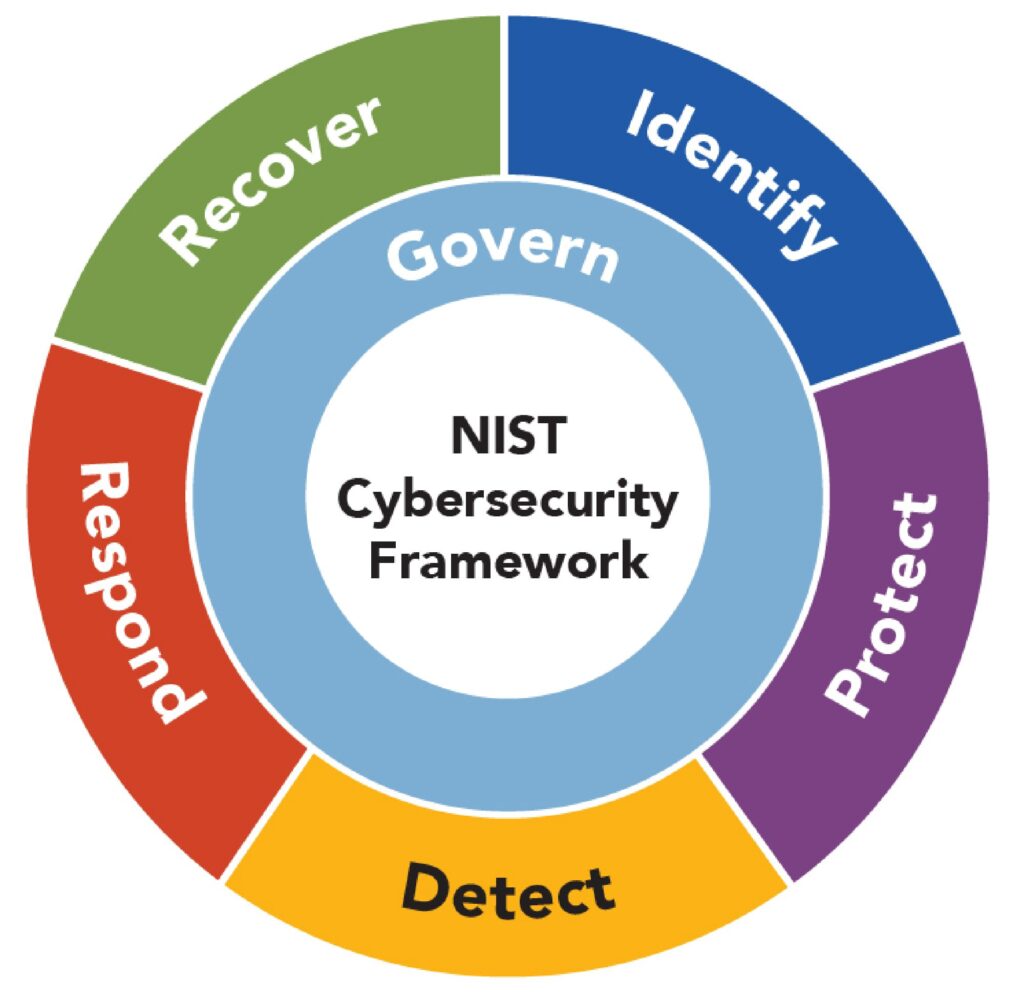
The NIST Cybersecurity Framework is a set of guidelines developed by the National Institute of Standards and Technology to help organizations manage and reduce cybersecurity risks. It provides a structured approach to identifying, protecting, detecting, responding to, and recovering from cyber threats, making it a widely accepted standard in cybersecurity planning. Hacking for Good can help your organization review and incorporate relevant practices from the framework to bolster your cybersecurity posture. Its importance lies in helping organizations build stronger defenses, improve incident response, and align their security practices with industry best practices. By following the framework, companies can better safeguard sensitive data, maintain customer trust, and meet regulatory requirements. Overall, the NIST Cybersecurity Framework serves as a valuable tool for building a resilient and proactive security posture in today’s increasingly digital world.
Related Post
The Cybersecurity Maturity Model Certification (CMMC) framework is a set of cybersecurity standards developed by the U.S. Department of Defense (DoD) to ensure that contractors and subcontractors properly protect sensitive government informationOrganizations working with the federal government are required to meet specific CMMC levels based on the nature of their work, making it an essential […]
Network Traffic Inspection
Network traffic inspection is the process of monitoring and analyzing the data that flows in and out of a nonprofit’s computer network. This includes emails, web activity, file transfers, and other communications between devices and external servers. For nonprofits, inspecting network traffic is a vital cybersecurity measure that helps detect suspicious behavior, prevent data breaches, […]
Simulated Phishing Exercises
A simulated phishing exercise is a cybersecurity training method used to test and educate employees about phishing threats. Hacking for Good can send fake but realistic phishing emails to organizational staff to see how they respond-whether they click on suspicious links, enter sensitive information, or report the email as suspicious, all in a safe and […]