Network traffic inspection is the process of monitoring and analyzing the data that flows in and out of a nonprofit’s computer network. This includes emails, web activity, file transfers, and other communications between devices and external servers. For nonprofits, inspecting network traffic is a vital cybersecurity measure that helps detect suspicious behavior, prevent data breaches, and protect sensitive information such as donor records, financial data, and internal communications. Cybercriminals often target nonprofits because they may have limited security resources but still handle valuable data. By examining traffic patterns, Hacking for Good can spot unusual activity like unauthorized access attempts or unsecured communication and recommend mitigations. Regular network traffic inspection strengthens a nonprofit’s overall security posture and builds trust with supporters by demonstrating a commitment to safeguarding their information.
Related Post
Online Footprint Review
An online footprint evaluation for a nonprofit is a cybersecurity-focused review of how much information the organization—and its staff, volunteers, and donors—are exposing publicly on the internet. This includes analyzing the nonprofit’s website, social media accounts, staff directories, event listings, and any other digital content that could reveal sensitive or exploitable details. While transparency is […]
Network Scanning
Network scanning is one of the first and most important steps in protecting a computer network from cyber threats. It’s the process of examining a network to discover all connected devices, open ports, and running services—essentially creating a map of everything that’s online. For IT administrators, this is a vital tool that helps them understand […]
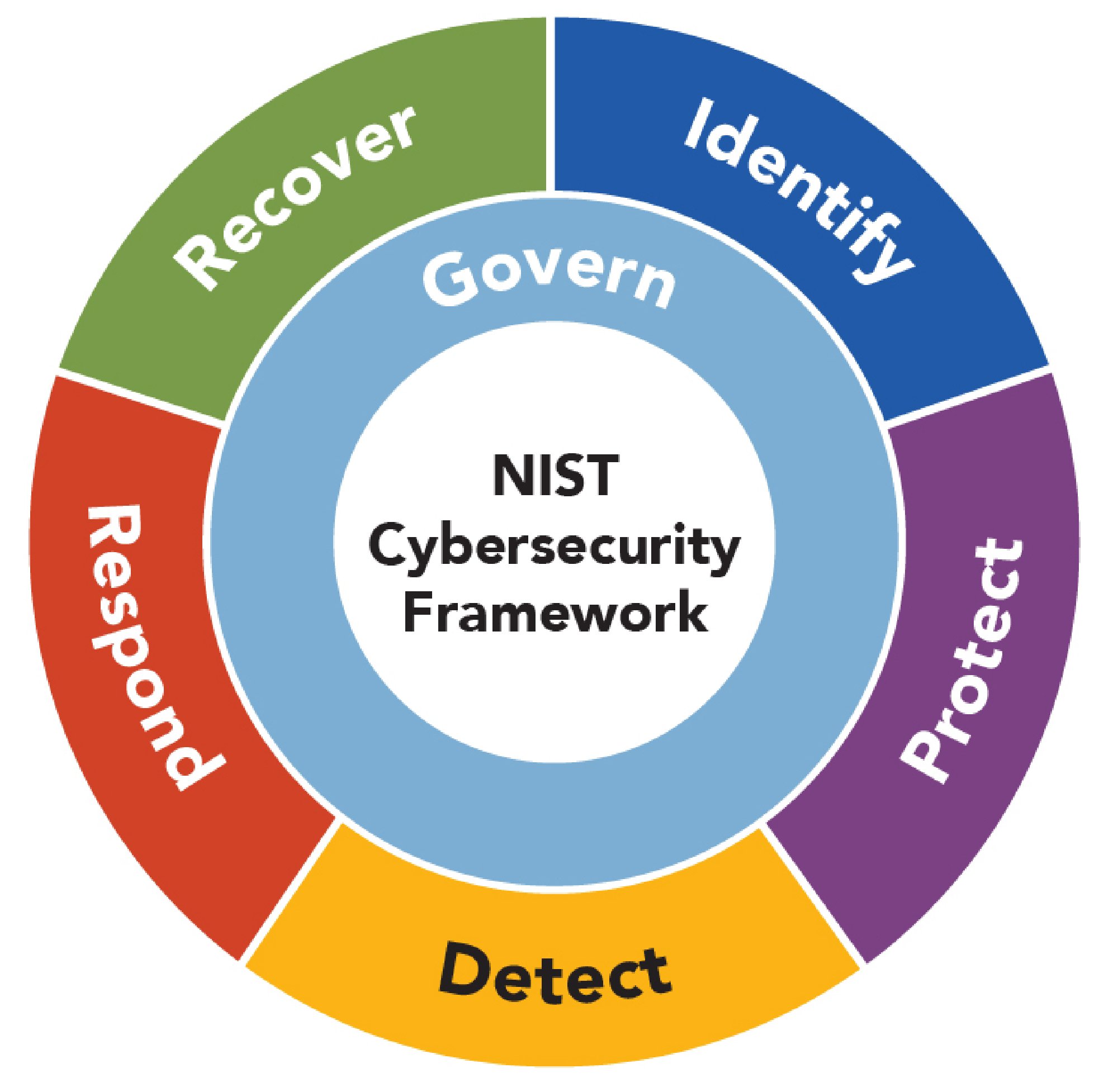
NIST Cybersecurity Framework
The NIST Cybersecurity Framework is a set of guidelines developed by the National Institute of Standards and Technology to help organizations manage and reduce cybersecurity risks. It provides a structured approach to identifying, protecting, detecting, responding to, and recovering from cyber threats, making it a widely accepted standard in cybersecurity planning. Hacking for Good can […]