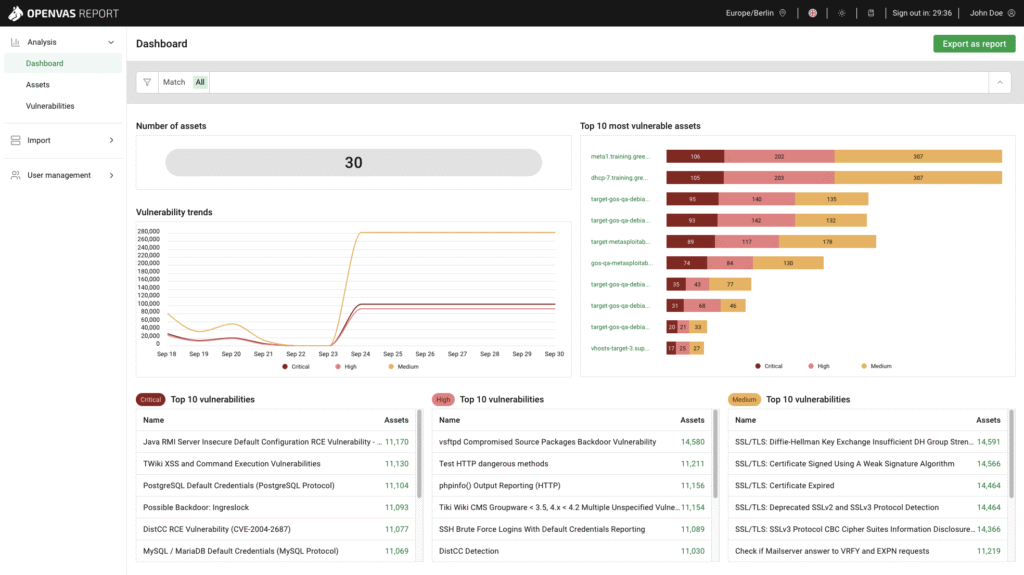
Network scanning is one of the first and most important steps in protecting a computer network from cyber threats. It’s the process of examining a network to discover all connected devices, open ports, and running services—essentially creating a map of everything that’s online. For IT administrators, this is a vital tool that helps them understand what’s on their network, how it’s configured, and where vulnerabilities might exist. Hacking for Good uses network scans to identify outdated software, misconfigured systems, or unauthorized devices that could be exploited by hackers. In short, network scanning gives IT admins the visibility and control they need to keep their systems secure, efficient, and resilient against evolving cyber threats. Not familiar? No problem! Hacking for Good provides a custom appliance to conduct the scans- simply plug it in to your network, power it on, and walk away!
Related Post
Network Traffic Inspection
Network traffic inspection is the process of monitoring and analyzing the data that flows in and out of a nonprofit’s computer network. This includes emails, web activity, file transfers, and other communications between devices and external servers. For nonprofits, inspecting network traffic is a vital cybersecurity measure that helps detect suspicious behavior, prevent data breaches, […]
The Cybersecurity Maturity Model Certification (CMMC) framework is a set of cybersecurity standards developed by the U.S. Department of Defense (DoD) to ensure that contractors and subcontractors properly protect sensitive government informationOrganizations working with the federal government are required to meet specific CMMC levels based on the nature of their work, making it an essential […]
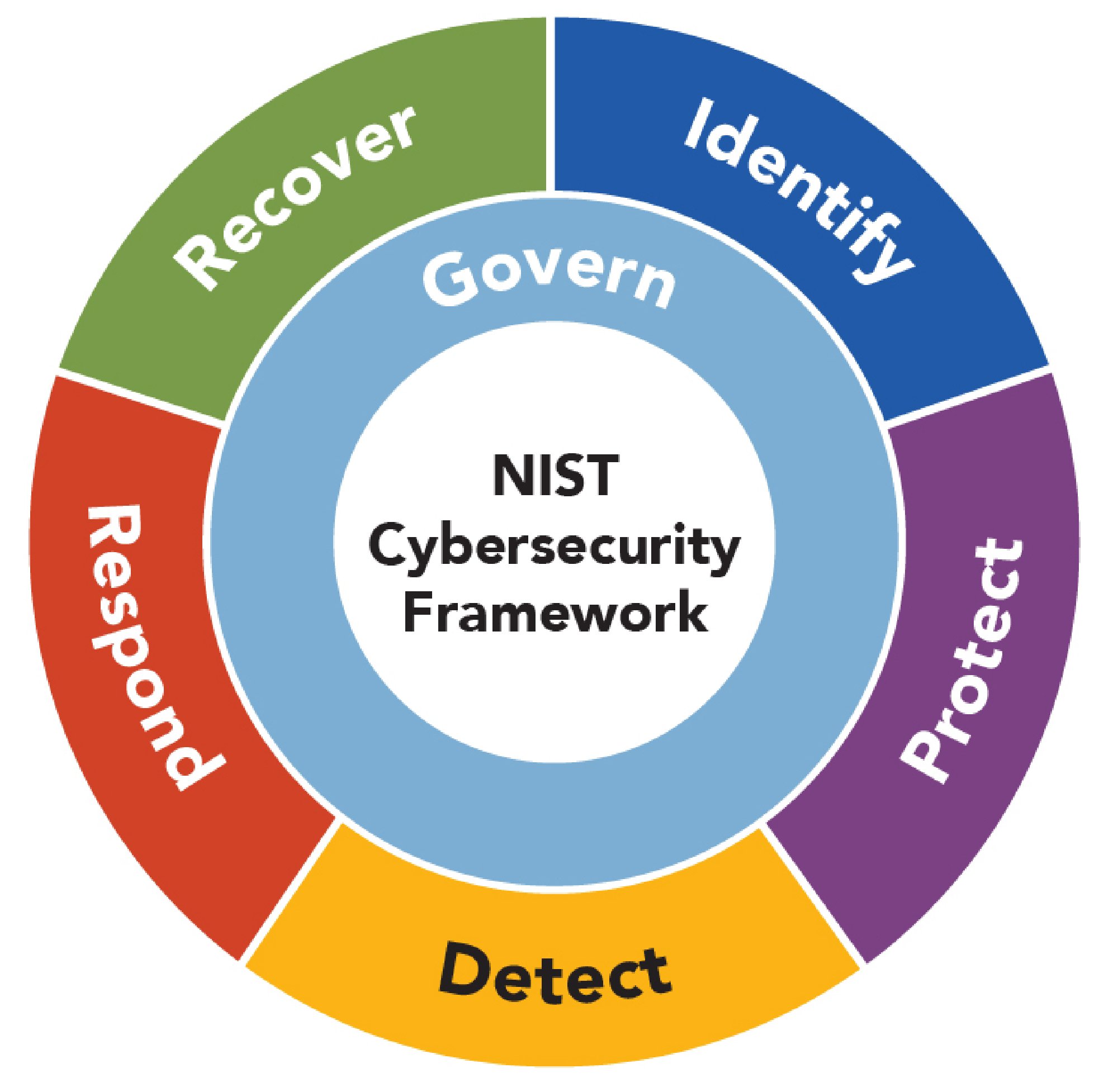
NIST Cybersecurity Framework
The NIST Cybersecurity Framework is a set of guidelines developed by the National Institute of Standards and Technology to help organizations manage and reduce cybersecurity risks. It provides a structured approach to identifying, protecting, detecting, responding to, and recovering from cyber threats, making it a widely accepted standard in cybersecurity planning. Hacking for Good can […]