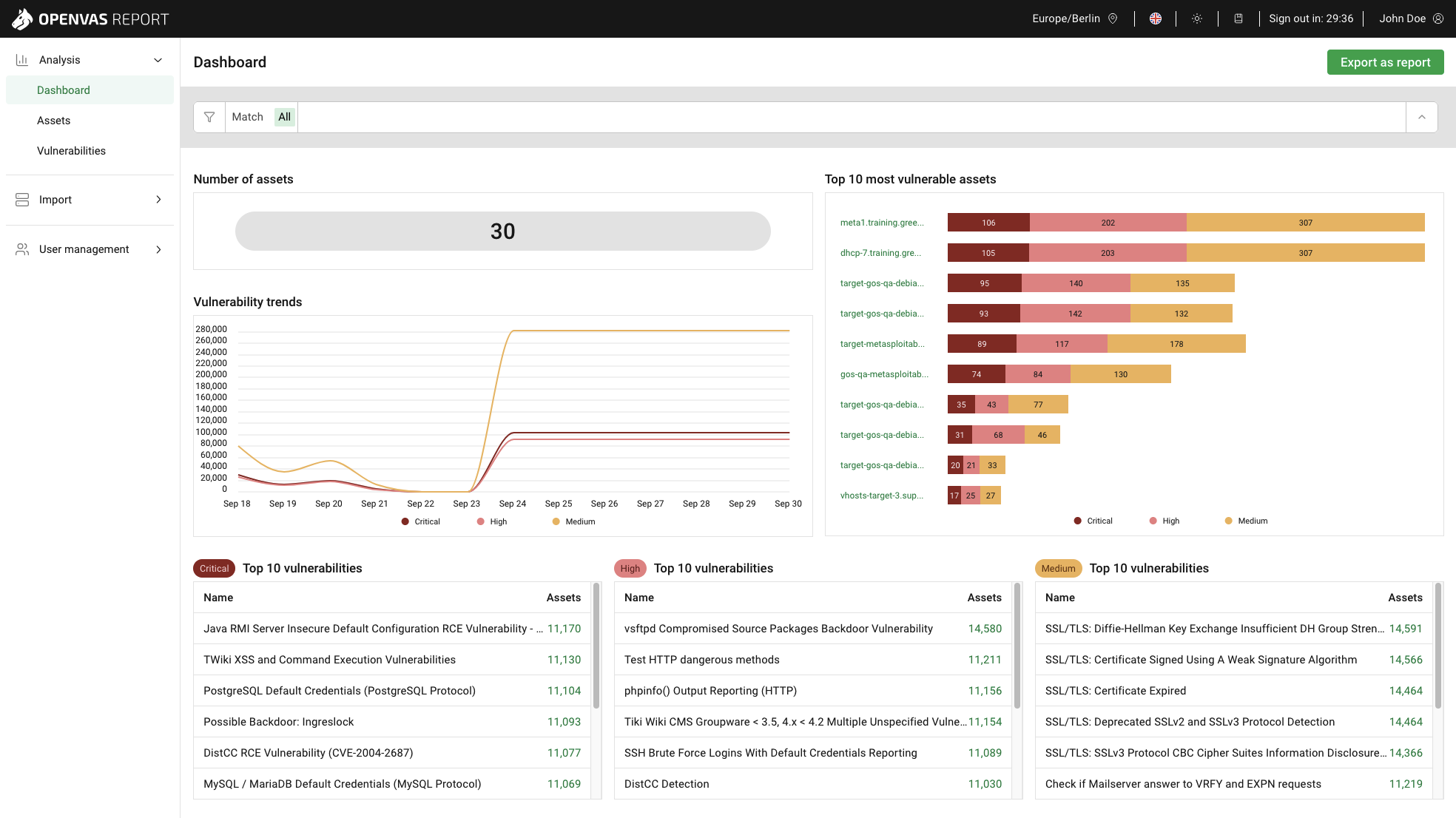
Everyone gets a login when they join an organization- what happens when they leave? Does everyone share the password to the company’s general inquiry email account? Can I connect my personal laptop to the company network? A cybersecurity policy review is a structured evaluation of an organization’s existing rules, procedures, and guidelines that govern how digital assets and sensitive information are protected. The process examines areas such as data privacy, access controls, password standards, incident response, and employee training to ensure they align with current best practices and regulatory requirements. By identifying gaps, outdated measures, or unclear responsibilities, the review helps strengthen resilience against cyber threats. Ultimately, it provides a roadmap for improving security posture, reducing risk, and fostering a culture of accountability and awareness across the organization, as well as ensuring leadership has clear, actionable guidance for making informed security decisions.
Related Post
Simulated Phishing Exercises
A simulated phishing exercise is a cybersecurity training method used to test and educate employees about phishing threats. Hacking for Good can send fake but realistic phishing emails to organizational staff to see how they respond-whether they click on suspicious links, enter sensitive information, or report the email as suspicious, all in a safe and […]
Network Scanning
Network scanning is one of the first and most important steps in protecting a computer network from cyber threats. It’s the process of examining a network to discover all connected devices, open ports, and running services—essentially creating a map of everything that’s online. For IT administrators, this is a vital tool that helps them understand […]
Online Footprint Review
An online footprint evaluation for a nonprofit is a cybersecurity-focused review of how much information the organization—and its staff, volunteers, and donors—are exposing publicly on the internet. This includes analyzing the nonprofit’s website, social media accounts, staff directories, event listings, and any other digital content that could reveal sensitive or exploitable details. While transparency is […]